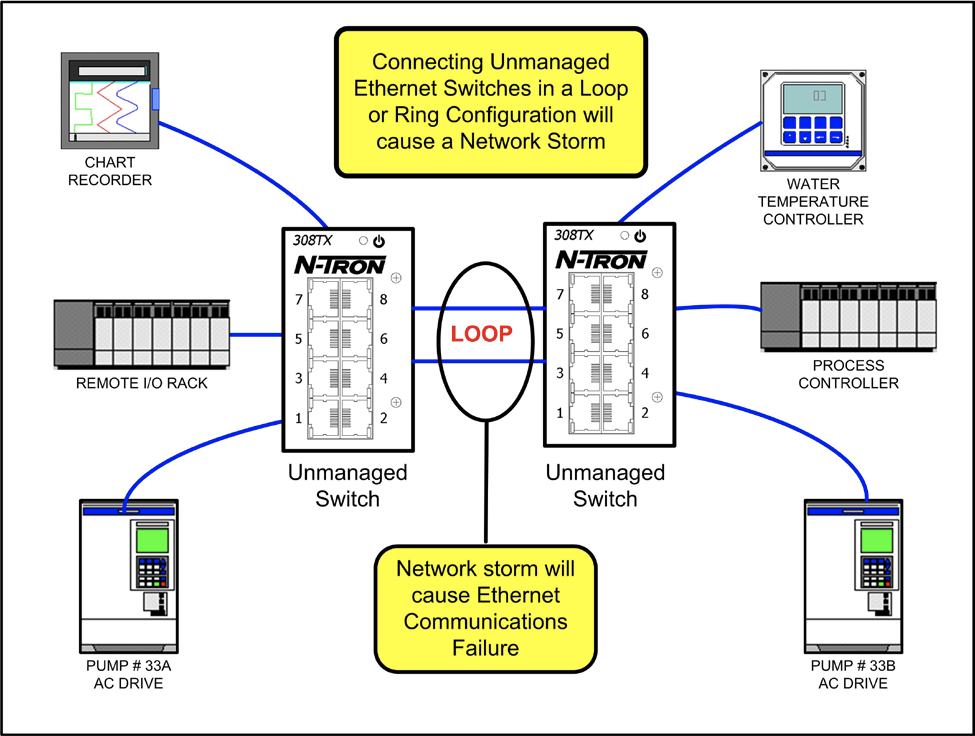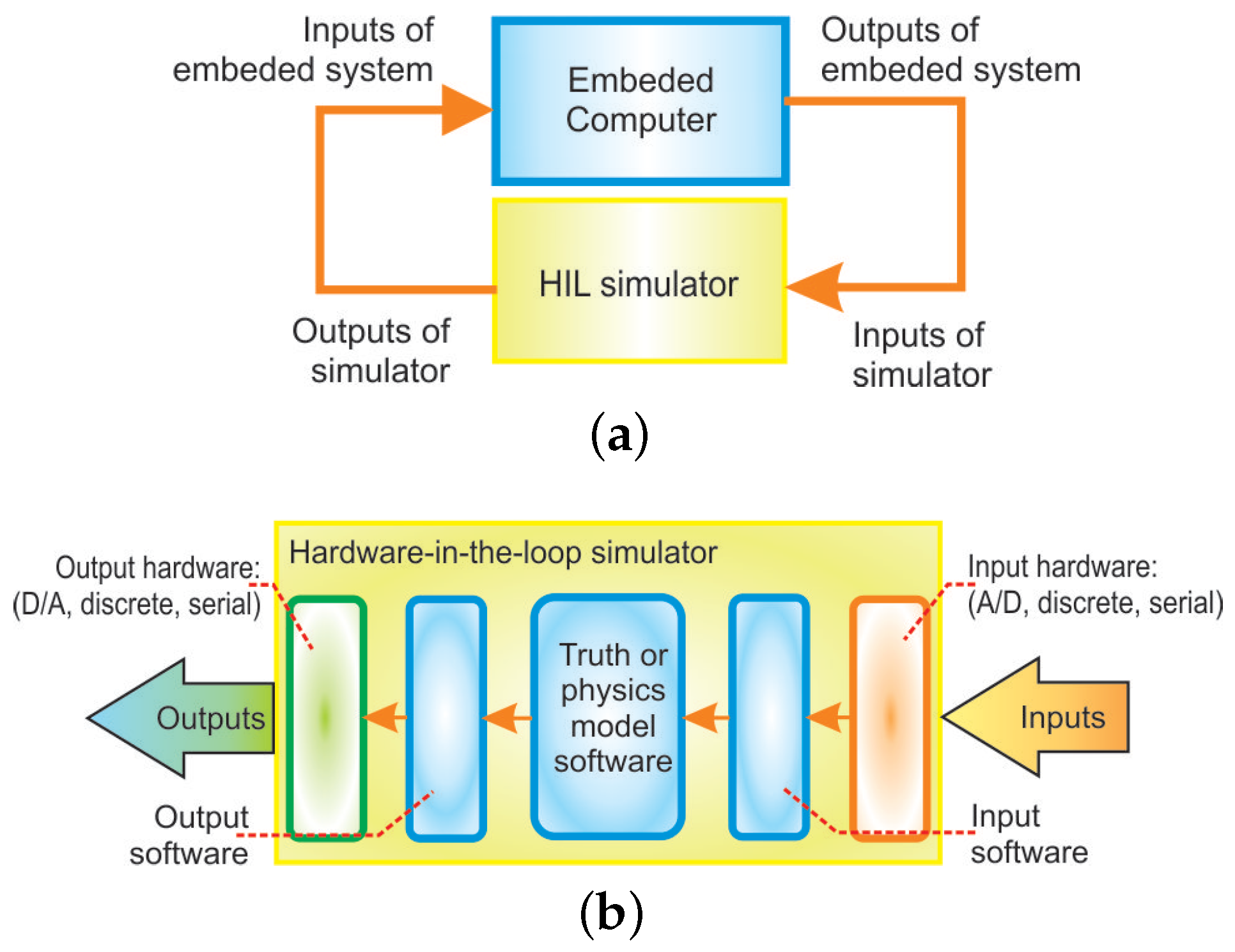
Electronics | Free Full-Text | Hardware-in-the-Loop Simulations: A Historical Overview of Engineering Challenges
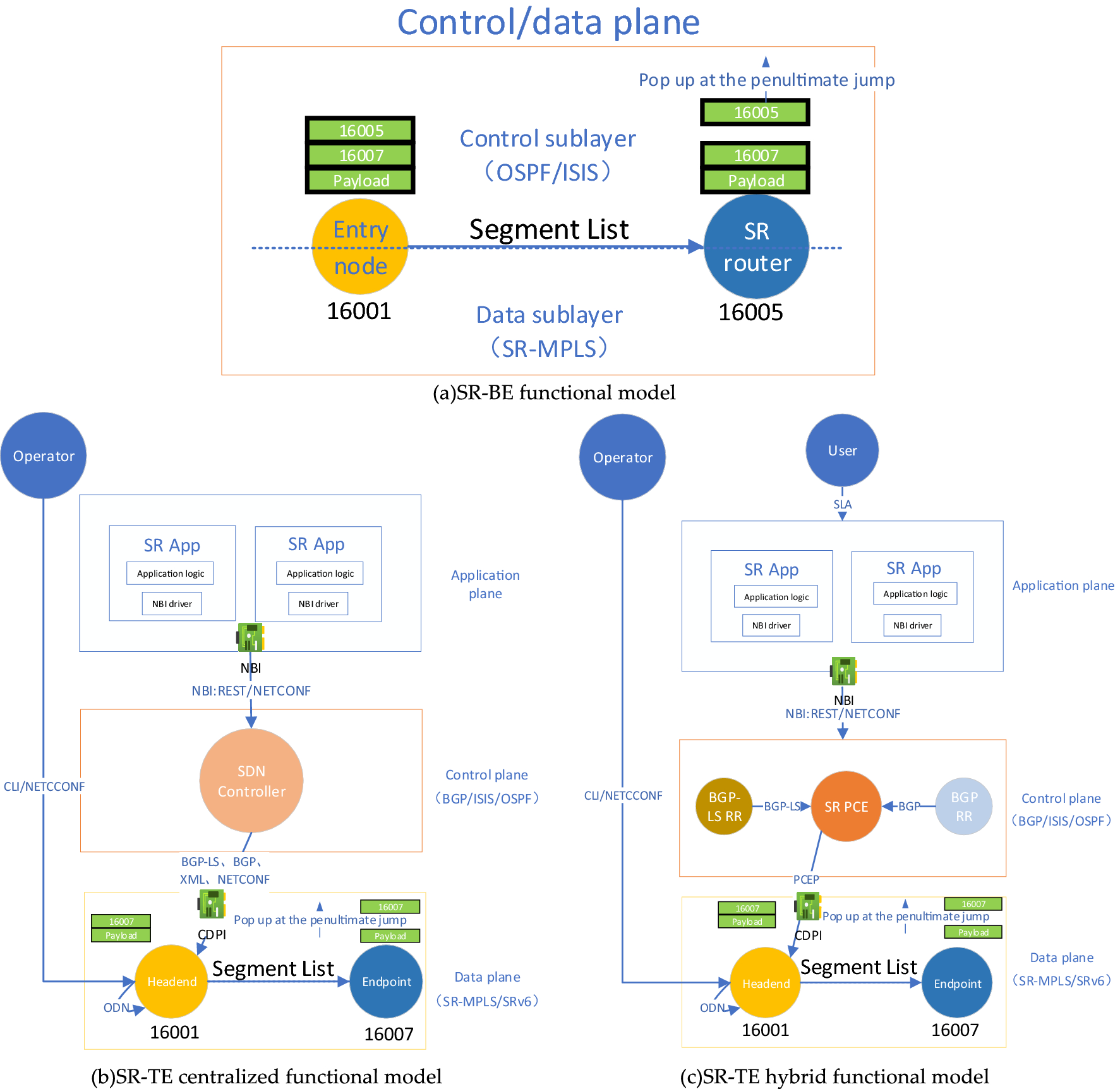
A data plane security model of segmented routing based on SDP trust enhancement architecture | Scientific Reports
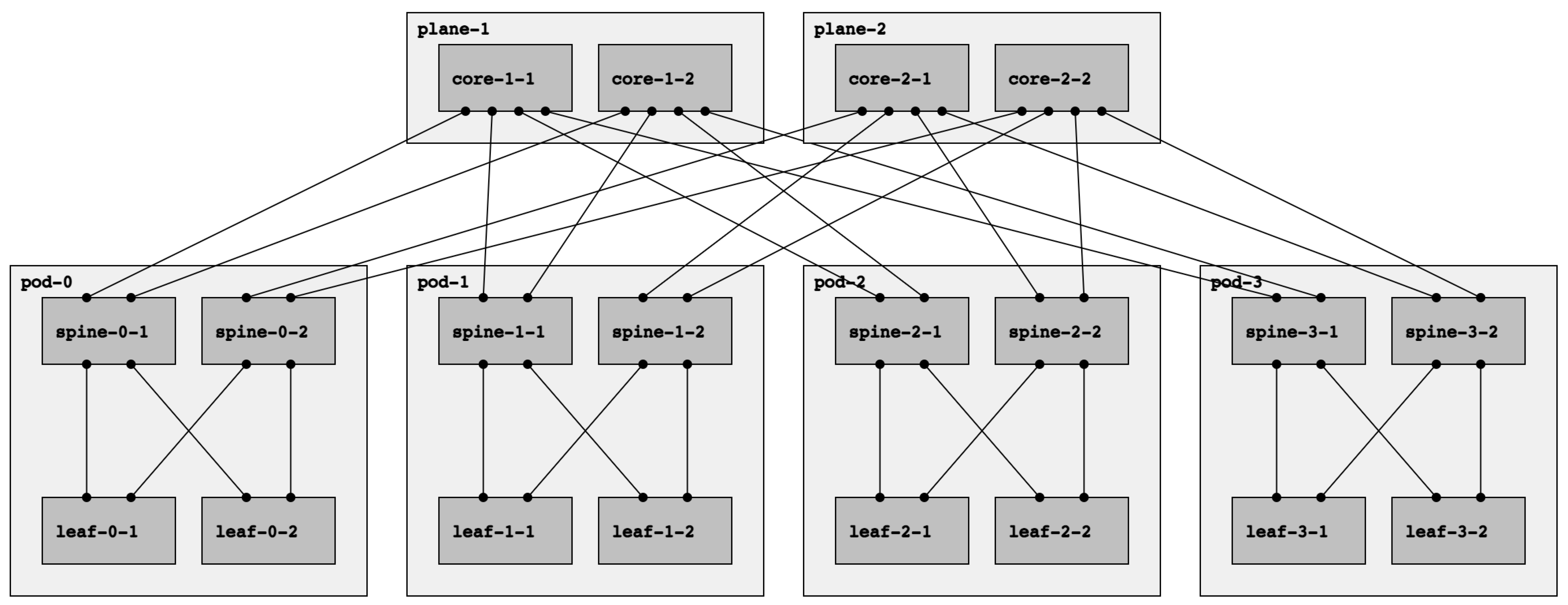
Future Internet | Free Full-Text | Experimentation Environments for Data Center Routing Protocols: A Comprehensive Review