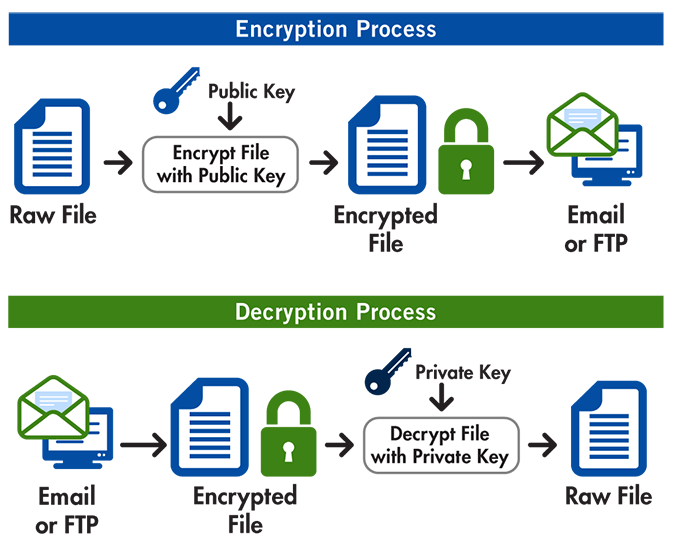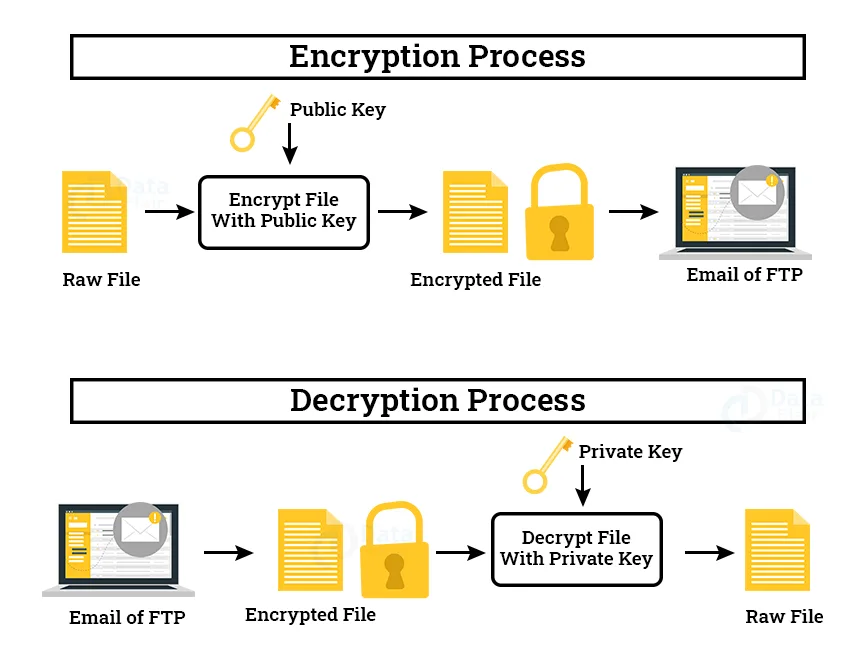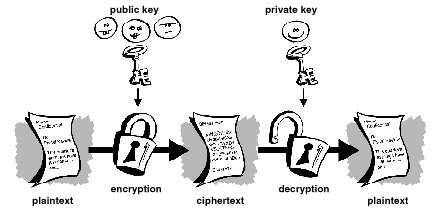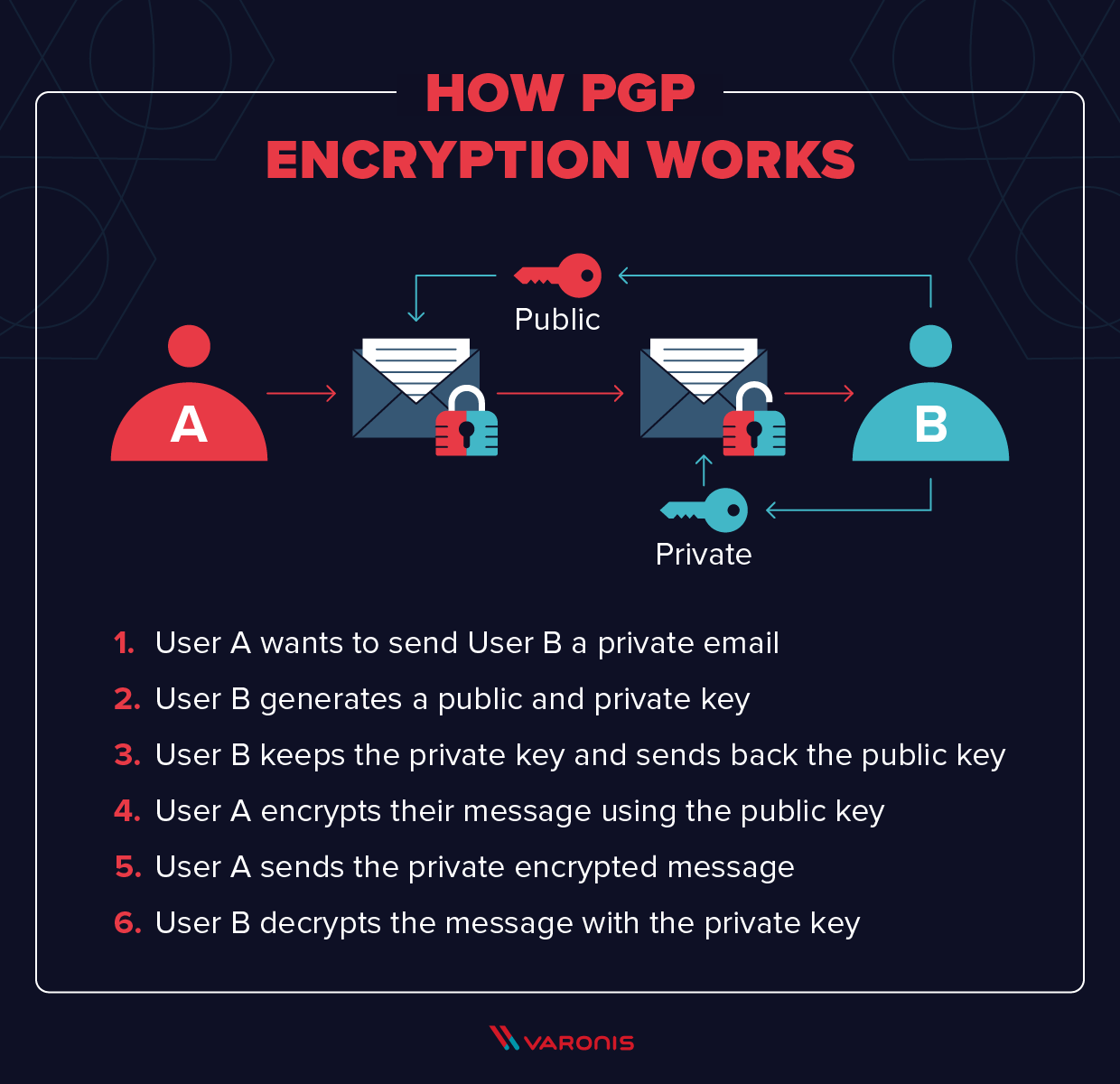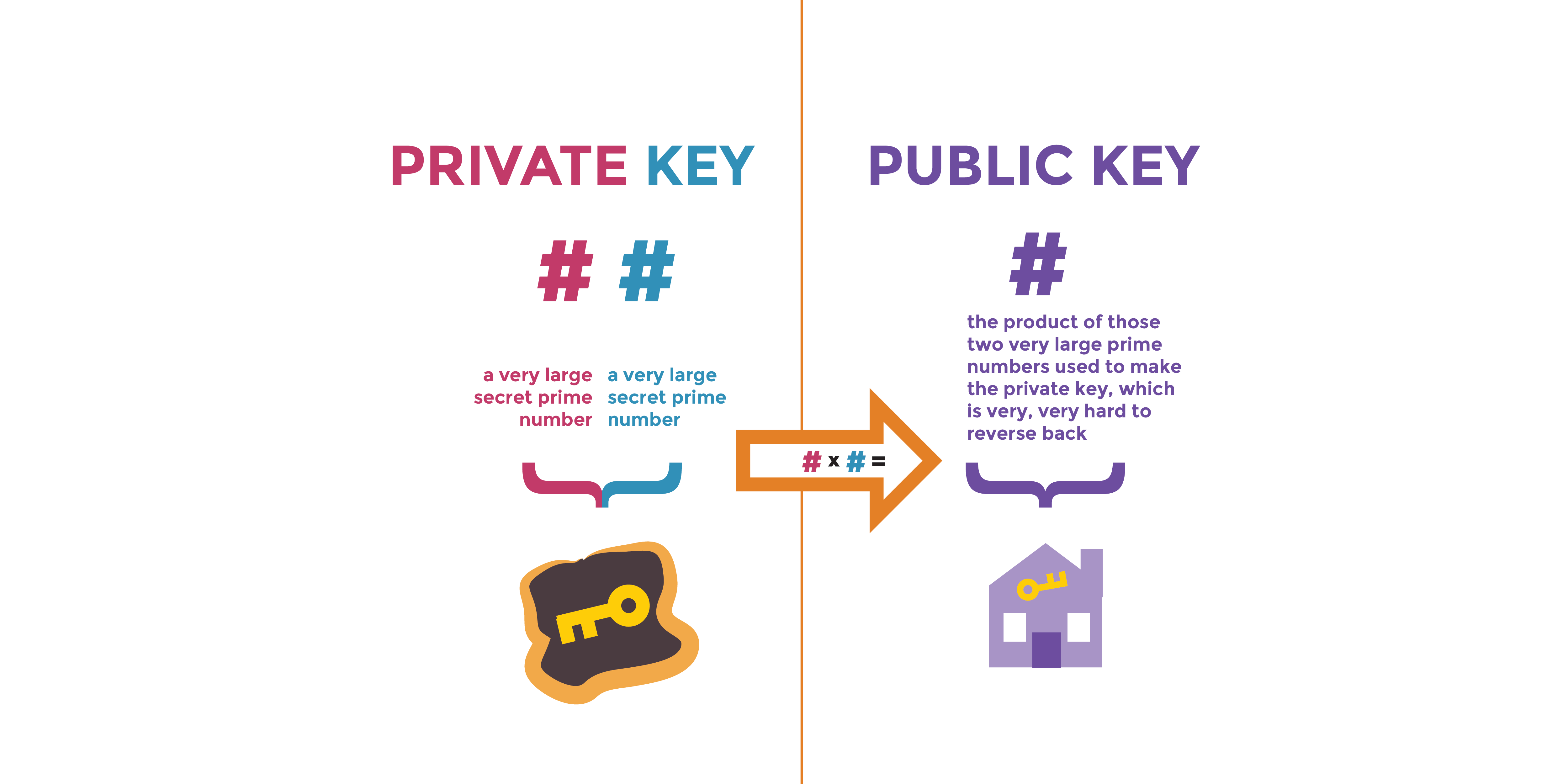
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense
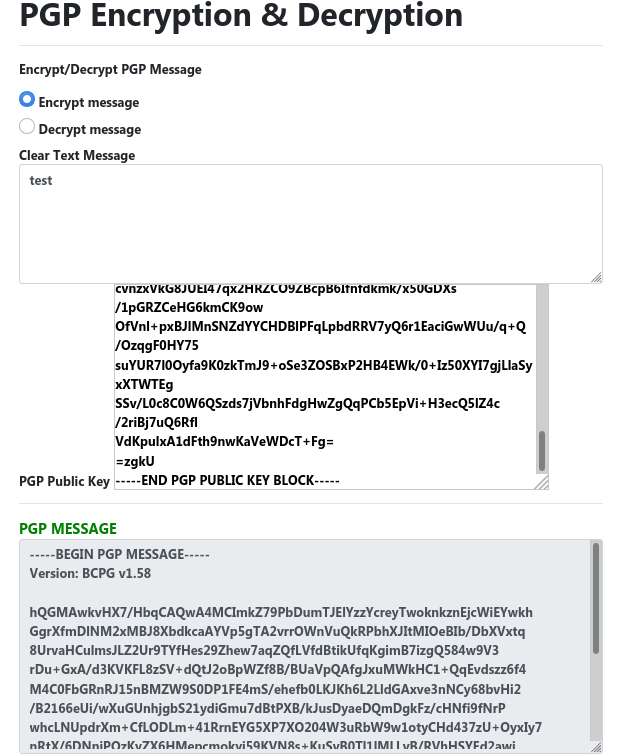
How To Make a PGP Keypair using GPG and Communicate In Absolute Privacy (Linux/Mac) Public & Private Keys + Encrypt & Decrypt Messages - Sick Codes - Security Research, Hardware & Software

pgp - Why is GnuPG changing first two characters of ascii armored public key after downloading it from the key server? - Cryptography Stack Exchange